Malware includes viruses, worms, Trojan horses, keyloggers, spyware, and adware. These are designed to invade privacy, steal information, damage the computer, or corrupt data. It is important that you protect computers and mobile devices using reputable antimalware software. Table 39-6 summarizes the types of antimalware programs that are available.

Table 39-6 Types of Antimalware Programs
Windows Defender Firewall (39.5.8)
A firewall selectively denies traffic to a computer or network segment. Firewalls generally work by opening and closing the ports used by various applications. By opening only the required ports on a firewall, you are implementing a restrictive security policy. Any packet not explicitly permitted is denied. In contrast, a permissive security policy permits access through all ports, except those explicitly denied. In the past, software and hardware were shipped with permissive settings. As users neglected to configure their equipment, the default permissive settings left many devices exposed to attackers. Most devices now ship with settings as restrictive as possible, while still allowing easy setup.
To allow program access through the Windows Defender Firewall, search for Control Panel, open it, and then locate and click Windows Defender Firewall to open it. Click Allow an app or feature through Windows Defender Firewall, as shown in Figure 39-17.
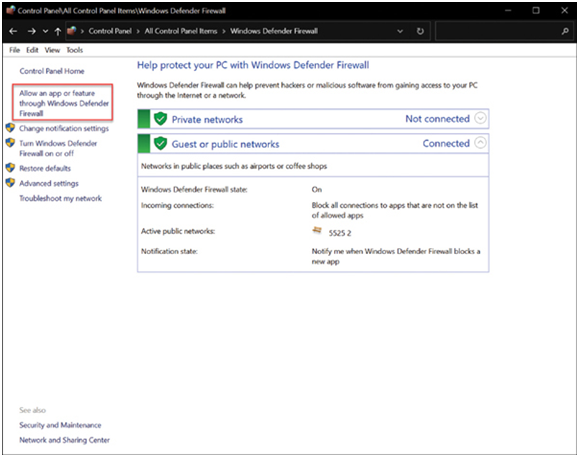
Figure 39-17 Allowing an App Access Through Windows Defender Firewall
If you wish to use a different software firewall, you will need to disable Windows Firewall. To disable the Windows Firewall, click Turn Windows Firewall on or off, as shown in Figure 39-18.
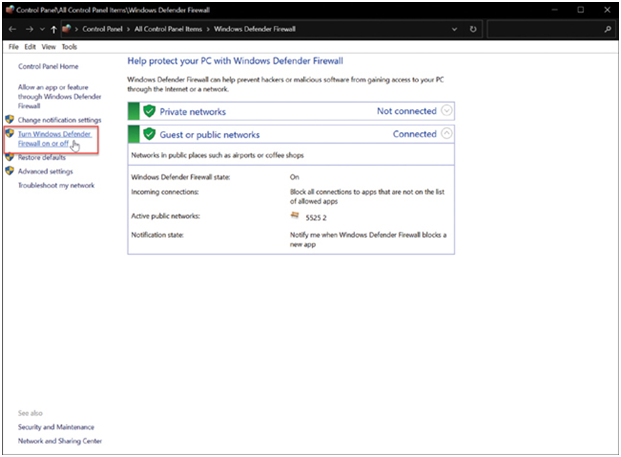
Figure 39-18 Turning Off Windows Defender Firewall
Windows Defender Firewall includes many additional features. Click Advanced settings to open them, as shown in Figure 39-19.
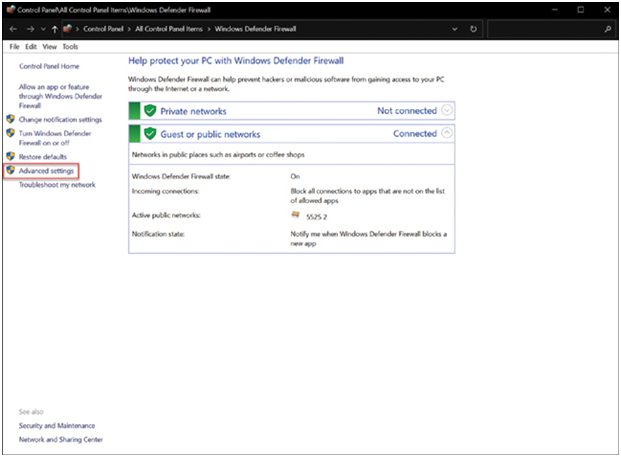
Figure 39-19 Accessing Advance Settings in Windows Defender Firewall
Here you can create inbound or outbound traffic rules based on different criteria. You can also import and export policies or monitor different aspects of the firewall, as shown in Figure 39-20.
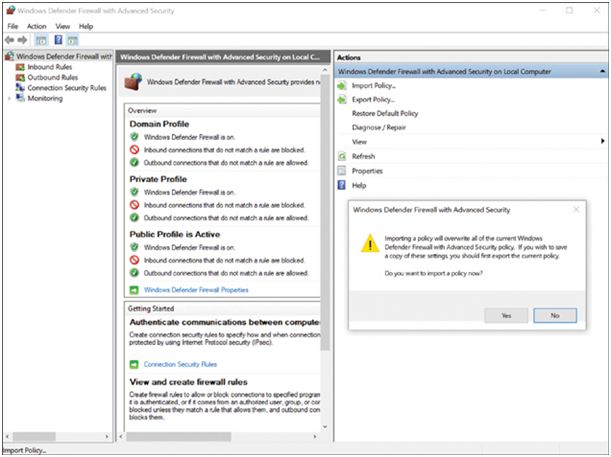
Figure 39-20 Importing a Policy in Windows Defender Firewall
Check Your Understanding—Firewall and Host-Based Intrusion Prevention (39.5.9)
Refer to the online course to complete this activity.
Secure Wireless Access (39.6)
Wireless networks introduce their own unique security concerns.
Video—WLAN Threats (39.6.1)
Wireless networks are growing rapidly. It is important to understand wireless network vulnerabilities, threats, and exploits.
Refer to the online course to view this video.
