The source and destination ports are placed within the segment. The segments are then encapsulated within an IP packet. The IP packet contains the IP address of the source and destination. The combination of the source IP address and source port number, or the destination IP address and destination port number is known as a socket.
In the example in Figure 15-4, the PC is simultaneously requesting FTP and web services from the destination server.
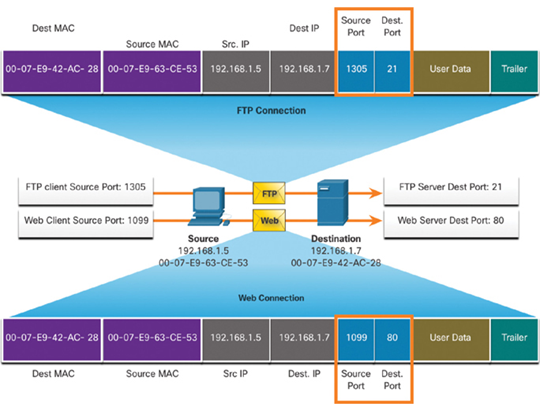
Figure 15-4 A Client and Server Use Port Numbers to Simultaneously Track FTP and Web Traffic
In the example, the FTP request generated by the PC includes the Layer 2 MAC addresses and the Layer 3 IP addresses. The request also identifies the source port number 1305 (dynamically generated by the host) and destination port, identifying the FTP services on port 21. The host also has requested a web page from the server using the same Layer 2 and Layer 3 addresses. However, it is using the source port number 1099 (dynamically generated by the host) and destination port identifying the web service on port 80.
The socket is used to identify the server and service being requested by the client. A client socket might look like this, with 1099 representing the source port number: 192.168.1.5:1099
The socket on a web server might be 192.168.1.7:80
Together, these two sockets combine to form a socket pair: 192.168.1.5:1099, 192.168.1.7:80
Sockets enable multiple processes, running on a client, to distinguish themselves from each other, and multiple connections to a server process to be distinguished from each other.
The source port number acts as a return address for the requesting application. The transport layer keeps track of this port and the application that initiated the request so that when a response is returned, it can be forwarded to the correct application.
Unexplained TCP connections can pose a major security threat. They can indicate that something or someone is connected to the local host. Sometimes it is necessary to know which active TCP connections are open and running on a networked host. Netstat is an important network utility that can be used to verify those connections. As shown in Example 15-1, enter the command netstat to list the protocols in use, the local address and port numbers, the foreign address and port numbers, and the connection state.
Example 15-1 Using the netstat Command to List Protocols in Use
C:\>
netstat
Active Connections
Proto Local Address Foreign Address State
TCP 192.168.1.124:3126 192.168.0.2:netbios-ssn
ESTABLISHED
TCP 192.168.1.124:3158 207.138.126.152:http
ESTABLISHED
TCP 192.168.1.124:3159 207.138.126.169:http
ESTABLISHED
TCP 192.168.1.124:3160 207.138.126.169:http
ESTABLISHED
TCP 192.168.1.124:3161 sc.msn.com:http
ESTABLISHED
TCP 192.168.1.124:3166 www.cisco.com:http
ESTABLISHED
(output omitted)
C:\>
By default, the netstat command will attempt to resolve IP addresses to domain names and port numbers to well-known applications. The -n option can be used to display IP addresses and port numbers in their numerical form.
Check Your Understanding – Port Numbers (15.2.5)
Refer to the online course to complete this activity.
