Review IAM permissions: You should not use a “set and forget” policy when it comes to your permissions in IAM. You should consistently review the permissions level assigned to ensure that you are following least privilege concepts and that you are still granting those permissions to the groups that require them. There is even a policy summary option within IAM to facilitate this.
Always configure a strong password policy for your users: It is a sad fact of human nature: Your users will tend to be lazy about setting (and changing) their passwords. They will tend to use simple passwords that are easy for them to remember. Unfortunately, these simple passwords are also easy to crack. Improve your security by setting a strong password policy that your users must adhere to. Figure 9-4 shows the configuration of a password policy for user accounts in the IAM Management Console.
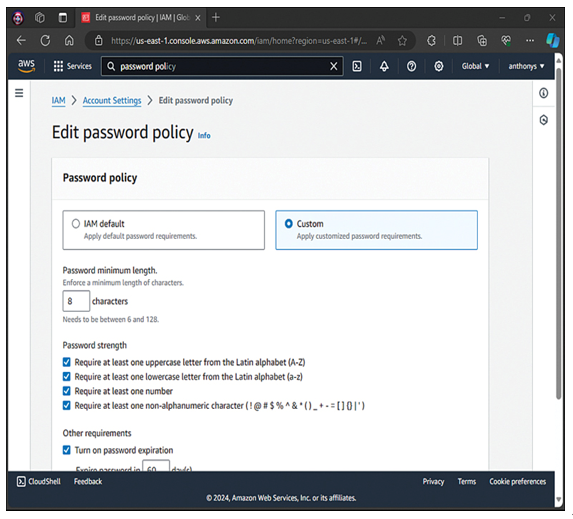
Figure 9-4 Configuring a Password Policy
Enable multifactor authentication for privileged user accounts: Of course, you already know to use MFA for the seldom-used AWS root account, but you should also protect key admin accounts you have created in AWS. Using MFA ensures that the user knows something (like a password) and also possesses something (like a smartphone). With most AWS environments today, MFA is considered mandatory.
Use roles: You should consider using roles in AWS when you have applications or services running on EC2 instances that need to access other services or resources.
Use roles to delegate permissions: Roles can also be very valuable when you need to permit one AWS account to access resources in another AWS account. This is a much more secure option than providing the other AWS account with username and password information for your account.
Do not share access keys: It might be tempting to share the access keys that permit programmatic access to a service or resource with another account that needs the same access. Resist this temptation. Remember that you can create a role that encompasses the required access.
Rotate credentials: Be sure to change passwords and access keys regularly in AWS. The reason for this, of course, is that if these credentials are compromised, you will have minimized the damage that can be done when the stolen credentials no longer function.
Remove unnecessary credentials: Because it is so easy to learn and test new features in AWS, it can get messy when you leave in place IAM components that are no longer needed. Be sure to routinely audit your resources for any “droppings” that are no longer needed. AWS even assists in this regard by structuring reports around credentials that have not been recently used.
Use policy conditions: Always consider building conditions into your security policies. For example, access might have to come from a select range of IP addresses. Or MFA might be required. Or there might need to be time-of-day or day-of-week conditions.
Monitor, monitor, monitor: AWS services provide the option for an intense amount of logging. Here are just some of the services where careful logging and analysis can dramatically improve security:
- CloudFront
- CloudTrail
- CloudWatch
- AWS Config
- S3
