Objectives
Upon completion of this chapter, you will be able to answer the following questions:
- What are foundational security concepts?
- How do you configure access control?
- What are the cybersecurity processes and procedures that protect systems?
- What are the methods of mitigating malware?
- How do firewalls operate to filter traffic and recommend endpoint security measures?
- How do you configure basic wireless security on a home router (WPAx)?
Key Terms
This chapter uses the following key terms. You can find the definitions in the Glossary.
availability
confidentiality
firewall
integrity
malware
Hello again! The awareness campaign that Lara worked on was a success. Because of this, the college has invited Lara to work on a committee to develop the college’s security policy. The security policy is a document that helps college administrators, IT staff, and college users defend the network and endpoints.
Lara will review current security policies on this committee and help develop new ones. These policies inform the IT staff how to keep data confidentiality, ensure data integrity, and ensure the network is available for all users. It also defines how the web can be accessed, which systems and devices will be used to secure it, and how to protect endpoint devices and wireless access. Let’s work through this chapter to learn more about what we can do to defend the network and its endpoints.
Security Foundations (39.1)
Security frameworks are used to give us a better understanding of network security.
The Cybersecurity Cube (39.1.1)
Have you heard of the cybersecurity cube? It provides a useful way to think about protecting data. The cube reminds us of what the task of protecting data entails, including the three dimensions of information security.
- Security Principles
The first dimension of the cybersecurity cube identifies the goals to protect cyberspace, as shown in Figure 39-1. The foundational principles of confidentiality, integrity, and availability of data provide a focus which enables the cybersecurity expert to prioritize actions when protecting any networked system.
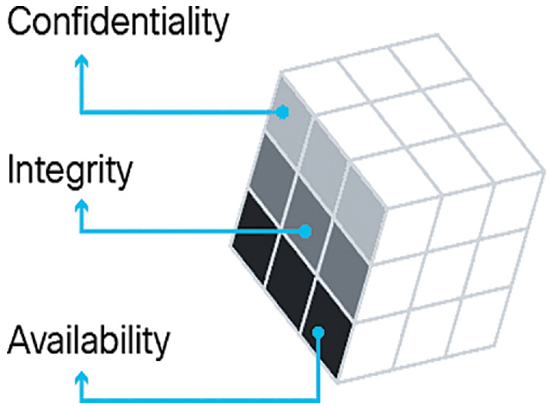
Figure 39-1 Security Principles of the Cybersecurity Cube
- Data confidentiality prevents the disclosure of information to unauthorized people, resources, or processes.
- Data integrity refers to the accuracy, consistency, and trustworthiness of data.
- Data availability ensures that information is accessible by authorized users when needed.
You can use the acronym CIA to remember these three principles.
- Data States
The cyberspace domain contains a considerable amount of critically important data. But in what state? The second dimension of the cybersecurity cube represents the three possible data states, as shown in Figure 39-2:
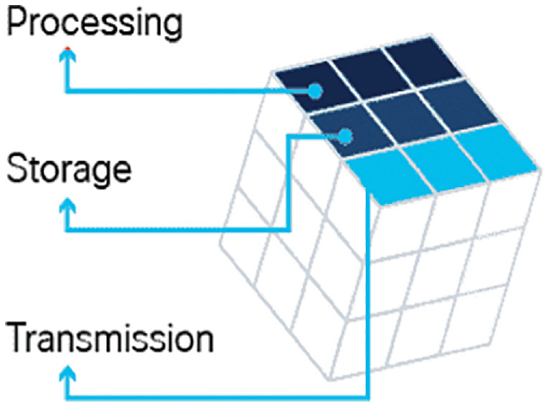
Figure 39-2 Data States of the Cybersecurity Cube
- Data in transit.
- Data at rest or in storage.
- Data in process.
Effective cybersecurity requires the safeguarding of data in all three states. We can’t focus only on protecting data that is being processed, nor just on data in storage.
- Safeguards
The third dimension of the cybersecurity cube defines the pillars on which we need to base our cybersecurity defenses in order to protect data and infrastructure in the digital realm, as shown in Figure 39-3.
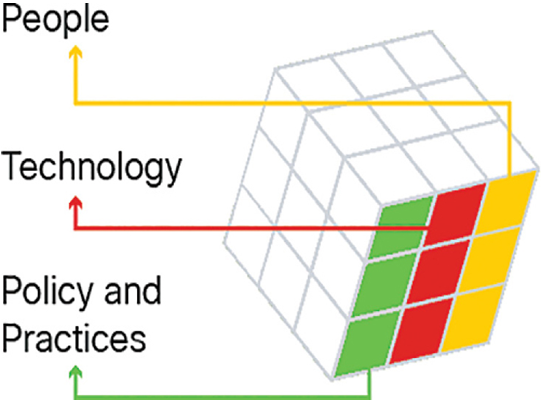
Figure 39-3 Safeguards of the Cybersecurity Cube
These are technology, policy and practices, and improving education, training, and awareness in people.
Cybersecurity professionals must use a range of different skills and disciplines available to them when protecting data and infrastructure in cyberspace.
