Skill 1.3: Manage Azure subscriptions and governance
An Azure subscription, which forms the core of an Azure environment, is a foundational component of every Azure implementation. Every resource that you create in Azure resides in an Azure subscription, which is a billing boundary for Azure resources with per-resource, role-based access controls.
As you build and deploy services in Azure, you will create many types of resources. For instance, when creating your first virtual machine, you will also deploy many other resources including
- A disk for the operating system
- A network interface for the VM
- A virtual network and subnet for that network interface to bind to
- A network security group (in a default portal configuration)
It is important to understand that many services in Azure create multiple resources, and how you manage those resources will be driven by organizational policy and the lifecycle of your infrastructure hosted in Azure.
A resource in Azure is a single-service instance, which can be a virtual machine, a virtual network, a storage account, or any other Azure service (see Figure 1-29).

FIGURE 1-29 Azure resource
Resource groups are logical groupings of resources or those single-service instances (Figure 1-30).
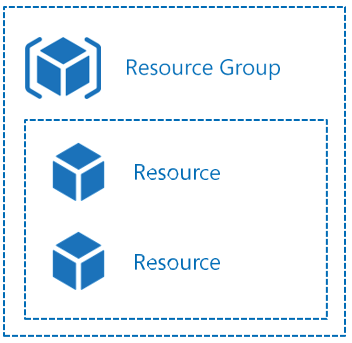
FIGURE 1-30 Azure hierarchy
Each resource in Azure can only exist in one resource group, and resource groups cannot be renamed. There are no limitations to the types of resources that can be logically contained within a resource group, and there are no limitations on the regions in which resources must reside when in a resource group.
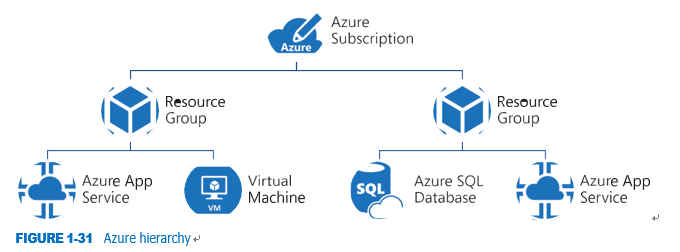
Figure 1-31 shows this hierarchy within an Azure subscription, multiple resource groups, and the resources that reside within those resource groups.
Azure Policy is an Azure service that can be used to create, assign, and manage policies that enforce governance in your Azure environment. This includes the application of rules that allow or deny a given resource type, apply tags automatically, and even enforce data sover- eignty. Azure RBAC and Azure Policy are often used in combination. Where Azure RBAC con- trols individual user access, group access, and rights to your Azure environments at a specific scope, Azure Policy provides a mechanism to express how the environment is governed for all users at a specified scope regardless of any RBAC assignments. Another way to state this is that Azure RBAC is a default deny mechanism with an explicit allow mechanism, whereas Policy is a default allow mechanism with an explicit deny system.
To implement Policy, a policy definition must first be authored. That policy definition is then assigned a specific scope using a policy assignment. Recall that scope refers to what your policy is assigned to with valid scopes, a management group, a subscription, a resource group, or a resource.
