The network infrastructure, services, and the data contained on network-attached devices are crucial personal and business assets. Network administrators must address two types of network security concerns: network infrastructure security and information security.
Securing the network infrastructure includes physically securing devices that provide network connectivity and preventing unauthorized access to the management software that resides on them, as shown in Figure 18-4.
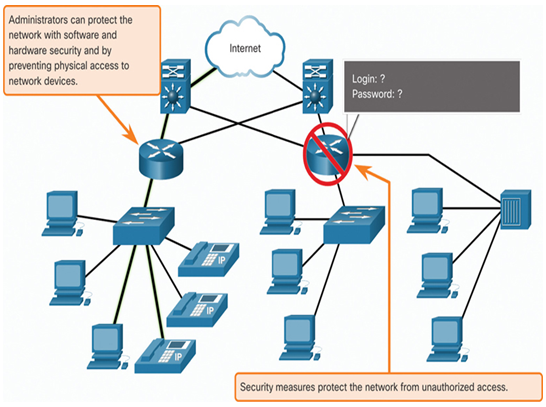
Figure 18-4 Security Design
Network administrators must also protect the information contained within the packets being transmitted over the network, and the information stored on network attached devices. In order to achieve the goals of network security, there are three primary requirements.
- Confidentiality – Data confidentiality means that only the intended and authorized recipients can access and read data.
- Integrity – Data integrity assures users that the information has not been altered in transmission, from origin to destination.
- Availability – Data availability assures users of timely and reliable access to data services for authorized users.
Check Your Understanding – Reliable Networks (18.1.7)
Refer to the online course to complete this activity.
Hierarchical Network Design (18.2)
This section explores the two different types of addresses: a logical address and a physical address. Both of these have a specific function in ensuring a message can be sent between two devices on the same network or between two devices on different networks.
Physical and Logical Addresses (18.2.1)
A person’s name usually does not change. A person’s address on the other hand, relates to where the person lives and can change. On a host, the MAC address does not change; it is physically assigned to the host NIC and is known as the physical address. The physical address remains the same regardless of where the host is placed on the network.
The IP address is similar to the address of a person. It is known as a logical address because it is assigned logically based on where the host is located. The IP address, or network address, is assigned to each host by a network administrator based on the local network.
IP addresses contain two parts. One part identifies the network portion. The network portion of the IP address will be the same for all hosts connected to the same local network. The second part of the IP address identifies the individual host on that network. Within the same local network, the host portion of the IP address is unique to each host, as shown in Figure 18-5.
Both the physical MAC and logical IP addresses are required for a computer to communicate on a hierarchical network, just like both the name and address of a person are required to send a letter.
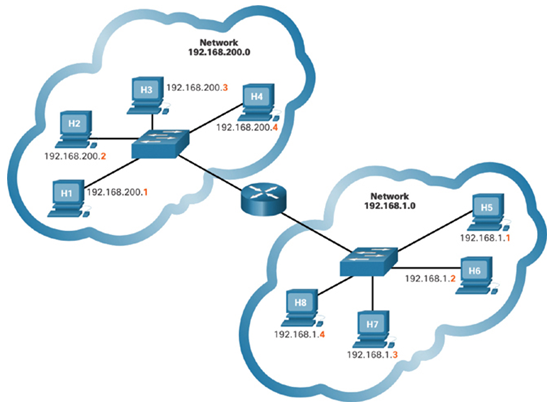
Figure 18-5 Network and Host Portion of the IPv4 Address
Video – View Network Information on My Device (18.2.2)
Refer to the online course to view this video.
Lab – View Wireless and Wired NIC Information (18.2.3)
In this lab, you will complete the following objectives:
- Identify and work with PC NICs.
- Identify and use the System Tray network icons.
Refer to the online course to complete this lab.
