Some AWS Security Features
I want to be perfectly clear: There are currently a ton of security services and tools in the AWS portfolio of products. In this section of the chapter, we will explore two that are fundamental to the operation of AWS: security groups and network access control lists (NACLs). We will also examine a third tool that is considered critical for organizations that are making web services and applications available via AWS: the Web Application Firewall (WAF) service.
Security Groups
Because security of your resources in the cloud is a prime concern for both you and Amazon, it is no big surprise that AWS provides built-in firewalls with your compute resources. These security groups help you easily control the accessibility of your EC2 virtual machine resources. Figure 10-1 shows an example of a security group assigned to a virtual network interface card in AWS.
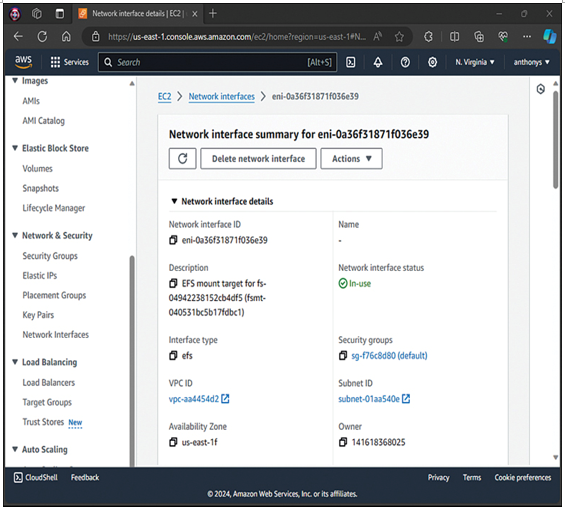
Figure 10-1 A Security Group Assigned to a virtual network interface card
Perhaps you have a web tier in your AWS architecture. You can configure the security group for this tier to permit HTTP and HTTPS traffic from customers using the web tier, and at the same time you can permit your team of support engineers to access the web tier using SSH and RDP. All other protocol attempts at accessing the web tier are denied by the security group.
You might wonder where security group are applied in AWS. AWS applies a security group by attaching it to the virtual network interface card (vNIC) of an EC2 virtual machine. This allows the security group to easily control (firewall) the traffic entering and exiting the EC2 instances.
Network ACLs (NACLs)
Network access control lists (NACLs) allow you to control access to your Virtual Private Cloud (VPC) subnets. NACLs are stateless constructs, which means you must configure inbound and outbound rules, as there is no automatic recognition of state with traffic flows, and there are no automated access entries.
Students are often puzzled about why these “firewalls” exist when there are already security groups inside AWS. Remember that security groups that are attached to virtual network interfaces of EC2 instances can control traffic to and from the virtual machines. NACLs are attached to subnets in a VPC to control traffic into and out of the entire subnet. Having multiple levels of built-in firewalls within the AWS network infrastructure permits fine-grained control of security.
Figure 10-2 shows an example of a NACL inside AWS.
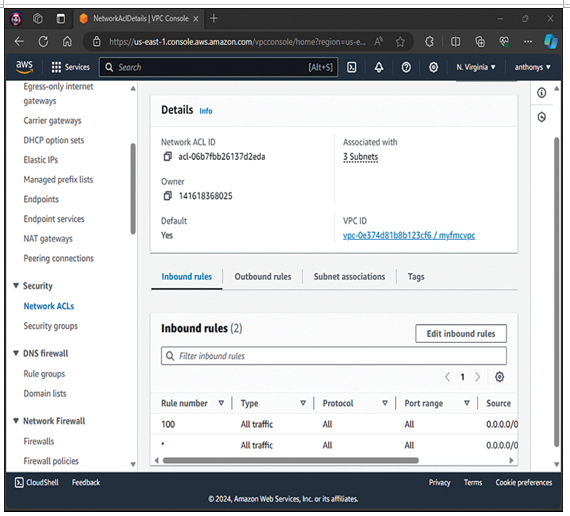
Figure 10-2 A NACL in AWS
