Wireless Security Overview (39.6.2)
A WLAN is open to anyone within range of a wireless access point (AP) and the appropriate credentials to associate to it. With a wireless NIC and knowledge of cracking techniques, an attacker may not have to physically enter the workplace to gain access to its network over a WLAN.
Attacks can be generated by outsiders, disgruntled employees, and even accidentally. Wireless networks are specifically susceptible to a number of threats, including:
- Interception of data—Wireless data should be encrypted to prevent it from being read by eavesdroppers.
- Wireless intruders—Unauthorized users attempting to access network resources can be deterred through effective authentication techniques.
- Denial of service (DoS) attacks—Access to WLAN services can be compromised either accidentally or maliciously. Various solutions exist depending on the source of the DoS attack.
- Rogue APs—Unauthorized APs installed by well-intentioned users, or for malicious purposes, can be detected using wireless network management software.
DoS Attacks (39.6.3)
Wireless DoS attacks can be the result of:
- Improperly configured devices—Configuration errors can disable the WLAN. For instance, an administrator could accidently alter a configuration and disable the network, or an intruder with administrator privileges could intentionally disable a WLAN.
- A malicious user intentionally interfering with the wireless communication—Their goal is to disable the wireless network completely or to the point where no legitimate device can access the medium.
- Accidental interference—WLANs are prone to interference from other wireless devices including microwave ovens, cordless phones, baby monitors, and more, as shown in Figure 39-21. The 2.4 GHz band is more prone to interference than the 5 GHz band.
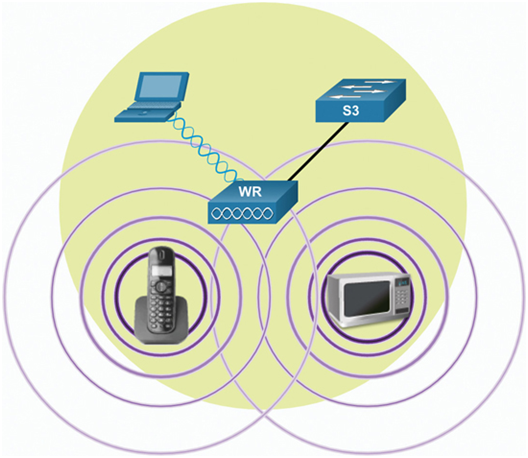
Figure 39-21 Example of Interference on the 5 GHz Band
To minimize the risk of a DoS attack due to improperly configured devices and malicious attacks, harden all devices, keep passwords secure, create backups, and ensure that all configuration changes are incorporated off-hours.
Monitor the WLAN for any accidental interference problems and address them as they appear. Because the 2.4 GHz band is used by other devices types, the 5 GHz band should be used in areas prone to interference.
A rogue AP is an AP or wireless router that has been connected to a corporate network without explicit authorization and against corporate policy. Anyone with access to the premises can install (maliciously or non-maliciously) an inexpensive wireless router that can potentially allow access to a secure network resource.
Once connected, the rogue AP can be used by an attacker to capture MAC addresses, capture data packets, gain access to network resources, or launch a man-in-the-middle attack.
A personal network hotspot could also be used as a rogue AP. For example, a user with secure network access enables their authorized Windows host to become a Wi-Fi AP. Doing so circumvents the security measures and enables other unauthorized devices to access network resources as a shared device.
To prevent the installation of rogue APs, organizations must configure wireless LAN controllers (WLCs) with rogue AP policies, as shown in Figure 39-22, and use monitoring software to actively monitor the radio spectrum for unauthorized APs.
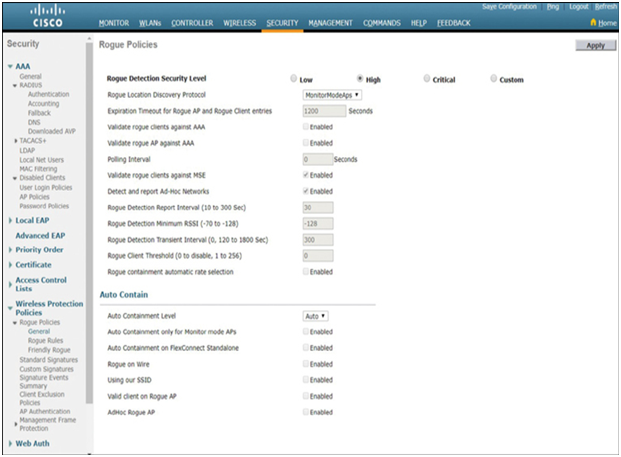
Figure 39-22 Configuring Rogue Policies on a Cisco WLC
