Types of Cyber Threats (38.1.2)
Cyber threats can be classified into different categories, as shown in Table 38-1. This allows organizations to assess the likelihood of a threat occurring and understand the monetary impact of a threat so that they can prioritize their security efforts.
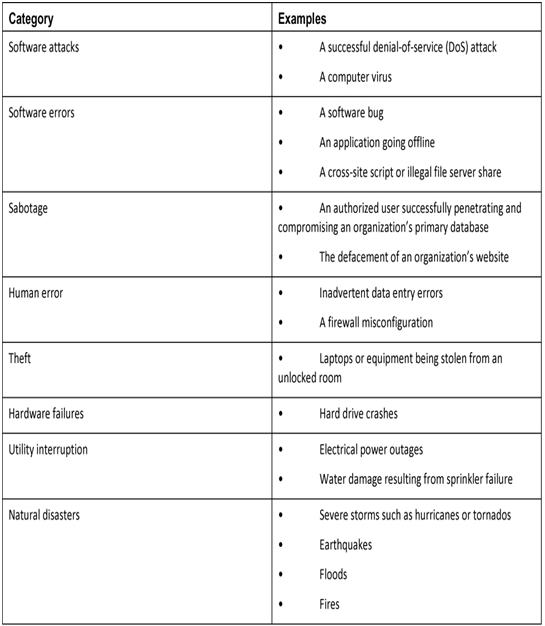
Table 38-1 Cyber Threat Categories and Examples
Internal vs. External Threats (38.1.3)
Threats can originate from both within and outside of an organization, with attackers seeking access to valuable sensitive information such as personnel records, intellectual property, and financial data, as shown in Figure 38-1.
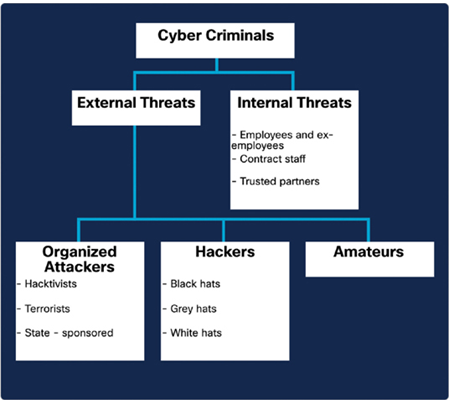
Figure 38-1 External and Internal Threats
Internal threats are usually carried out by current or former employees and other contract partners who accidentally or intentionally mishandle confidential data or threaten the operations of servers or network infrastructure devices by connecting infected media or by accessing malicious emails or websites.
The source of an external threat typically stems from amateur or skilled attackers who can exploit vulnerabilities in networked devices or can use social engineering techniques, such as trickery, to gain access to an organization’s internal resources.
Practice Item—Threat Origination (38.1.4)
Refer to the online course to complete this activity.
User Threats and Vulnerabilities (38.1.5)
A user domain includes anyone with access to an organization’s information system, including employees, customers, and contract partners. Users are often considered to be the weakest link in information security systems, posing a significant threat to the confidentiality, integrity, and availability of an organization’s data.
Table 38-2 lists the most common user threats to organizations.
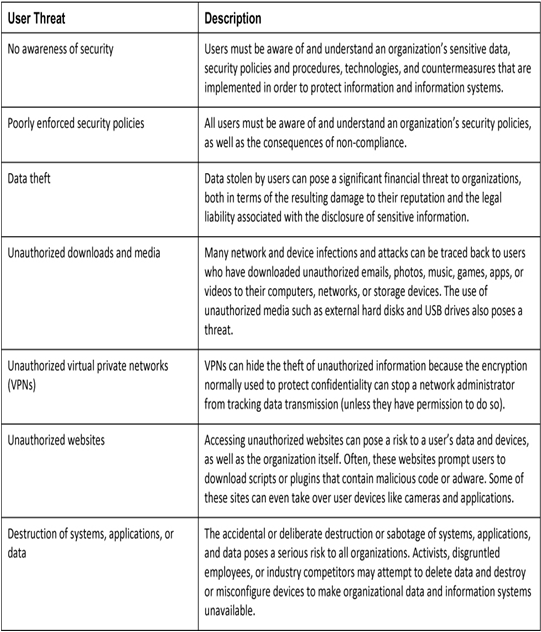
Table 38-2 User Threats to Organizations
Always keep in mind that there are no technical solutions, controls, or countermeasures that will make information systems any more secure than the behaviors and processes of the people who use these systems.
The following are common threats to devices:
- Any devices left powered on and unattended pose the risk of someone gaining unauthorized access to network resources.
- Downloading files, photos, music, or videos from unreliable sources could lead to the execution of malicious code on devices.
- Cybercriminals often exploit security vulnerabilities within software installed on an organization’s devices to launch an attack.
- An organization’s information security teams must try to keep up to date with the daily discovery of new viruses, worms, and other malware that pose a threat to their devices.
- Users who insert unauthorized USB drives, CDs, or DVDs run the risk of introducing malware, or compromising data stored on their device.
- Policies are in place to protect an organization’s IT infrastructure. A user can face serious consequences for purposefully violating such policies.
- Using outdated hardware or software makes an organization’s systems and data more vulnerable to attack.
